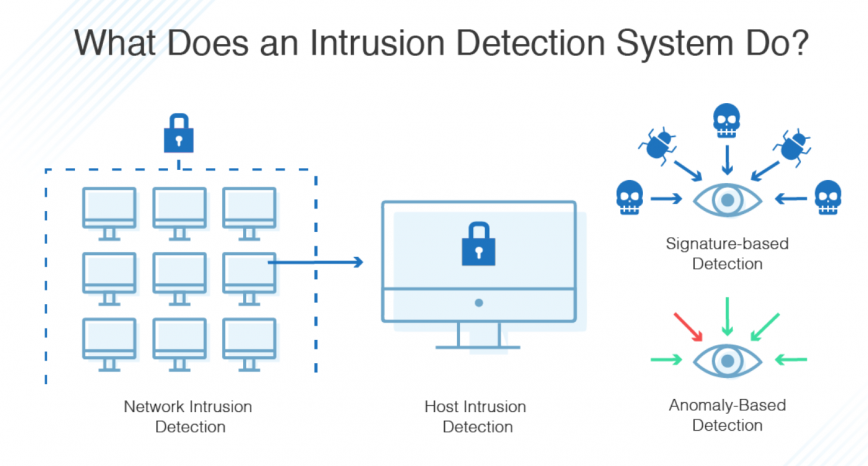
IDS Stands for “Intrusion Detection System.” An IDS monitors network traffic for suspicious activity. It may be comprised of hardware, software, or a combination of the two. IDSes are similar to firewalls, but are designed to monitor traffic that has entered a network, rather than preventing access to a network entirely. This allows IDSes to detect attacks that originate from within a network.
IDS – Intrusion Detection System
An intruder detection systems can be configured for either a network or a specific device. A network intrusion detection system (NIDS) monitors inbound and outbound traffic, as well as data transfers between systems within a network. NIDSes are often spread out across several different points in a network to make sure there a no loopholes where traffic may be unmonitored.
An IDS configured for a single device is called a host intrusion detection system, or HIDS. It monitors a single host for abnormal traffic patterns. For example, it may look for known viruses or malware in both inbound and outbound traffic. Some HIDSes even check packets for important system files to make sure they are not modified or deleted.
Both network and host IDSes are designed to detect intrusions and sound an alert. This alert may be sent to a network administrator or may be processed by an automated system. A system that automatically handles intrusion alerts is called a reactive IDS or an intrusion prevention system (IPS).